17/08/2018

When police ripped Hoffman’s shirt off his back they found he had a Viet Cong flag painted on his skin! pic from www.racked.com
You might have thought that an American wearing a shirt with the stars and stripes on it would be considered patriotic. Right?
Wrong! In 1968, Abbie Hoffman, co-founder of the Youth International Party was arrested in Washington for wearing a shirt that resembled the design of an American flag.
The prison authorities treated him badly for his “desecration” of the oh-so-blessed flag:
Authorities at the maximum security penitentiary did their worst to harass and humiliate him. They gave him a preventive de-lousing. They took a blood sample against his will, without affording him the sterile courtesy of a disposable syringe.
Two months later, Abbie was hospitalized in New York City for serum hepatitis. The recuperative process didn’t prevent him from helping doctors to organize themselves against some of the oppressive tactics of the medical profession.
(https://www.huffingtonpost.com/paul-krassner/the-trial-of-abbie-hoffma_b_2334.html)
In court, Hoffman’s lawyer asked how wearing a flag-shirt could be dishonouring the flag. “Does Uncle Sam, when he marches in the parade on July 4th, dishonor?”
The prosecutor shot down that line of reasoning. “Uncle Sam himself is a national symbol, just as the the flag is a national symbol, and one national symbol, recognized as such, cannot deface and defile and cast contempt upon another national symbol.”
Of course it was a load of crap, a prosecution out to get him because of who he was, a prominent Yippie advocating squatting and use of drugs. Plenty of clothing features flags in their design, but Hoffman is the first and only person to be arrested for wearing a flag shirt and charged with desecration of a flag.
Abbie Hoffman courted controversy and was fine with breaking the law. He wrote a book on how to survive with no money – he titled it Steal this Book. Plenty of would-be readers followed his sage advice and stole copies, leading to a number of book shops refusing to stock it.
In 1973 he was arrested and charged for possession and supply of cocaine when he made a drug deal with undercover police. So in 1974 he went on the run and the police failed to track him down – even though he was hardly keeping a low profile, helping coordinate an environmental movement seeking to protect the Saint Lawrence River, and writing as the “travel” columnist for Crawdaddy magazine under name pseudonym Barry Freed US Sen. Daniel Patrick Moynihan, before whom Hoffman testified at a hearing about winter navigation, said he had no idea the environmental posing as Freed was Hoffman — “and no one else did either.”
He turned himself in eventually, in 1980, and ended up serving four months.
According to ABC News, “the Yippies were known for street theater pranks, and were once referred to as the ‘Groucho Marxists’.” Hoffman himself described his views like this:
You are talking to a leftist. I believe in the redistribution of wealth and power in the world. I believe in universal hospital care for everyone. I believe that we should not have a single homeless person in the richest country in the world. And I believe that we should not have a CIA that goes around overwhelming governments and assassinating political leaders, working for tight oligarchies around the world to protect the tight oligarchy here at home.
In 1989 Hoffman killed himself by taking 150 phenobarbital tablets and liquor. I’m sure he had his reasons – as he did for everything else he ever did.
“Free speech means the right to shout ‘Theater’ in a crowded fire.”
“The first duty of a revolutionist is to get away with it. The second duty is to eat breakfast.”

 Leave a Comment » |
Leave a Comment » |  Abbie Hoffman, OMG, politics, Yippies, Youth International Party | Tagged: Abbie Hoffman, barry freed, free speech, politics, stars and stripes, USA, Yippies, Youth International Party |
Abbie Hoffman, OMG, politics, Yippies, Youth International Party | Tagged: Abbie Hoffman, barry freed, free speech, politics, stars and stripes, USA, Yippies, Youth International Party |  Permalink
Permalink
 Posted by Martin X
Posted by Martin X
11/08/2018
A woman detained in the UAE after drinking wine on an Emirates flight has been released.
Ellie Holman from Kent was arrested after accepting a complimentary glass of wine on her flight to Dubai. She says she was mistreated while in custody: she and her daughter were refused permission to go to the toilet for some time.
She was finally freed “on Sheikh Mohammed’s orders” and told she was welcome to go back to the UAE at any time.
Such mistreatment eh! She’s not allowed to go to the toilet! In the meantime, local criminals are getting flogged for alcohol consumption. And that’s far from the worst that can happen: for some crimes you can expect to get death by stoning.
Maybe pampered tourists who cry when they can’t use the toilet should go on holiday somewhere else? Maybe by going to the UAE and other countries under Sharia law, they are tacitly encouraging these medieval punishments? Then again, maybe not. If you want to go to the UAE and expect to be immune from the local laws, you’ll probably be okay. Western tourists aren’t usually punished for these crimes. Or at worst expect to be deported. Locals can expect the full fury of the law. But that doesn’t matter, does it? As long as you can enjoy a drink without any inconvenience…

 Leave a Comment » |
Leave a Comment » |  alcohol, crime, Ellie Holman, OMG, Sharia, UAE, United Arab Emirates | Tagged: alcohol, crime, Ellie Holman, Islam, Sharia, UAE, United Arab Emirates |
alcohol, crime, Ellie Holman, OMG, Sharia, UAE, United Arab Emirates | Tagged: alcohol, crime, Ellie Holman, Islam, Sharia, UAE, United Arab Emirates |  Permalink
Permalink
 Posted by Martin X
Posted by Martin X
02/08/2018

Reddit – “hacked”
Reddit member info was compromised in June this year. Two data-sets were accessed: the first from 2007 containing account details and all public and private posts between 2005 and May 2007; and the second included logs and databases linked to Reddit’s daily digest emails, which was accessed between 3 and 17 June this year. The data includes usernames and email addresses linked to those accounts.
Reddit they are contacting members who may have been affected. But the way these stories go, it will be revealed soon that everyone’s data has been leaked, so all Reddit members should probably reset their passwords.
And if you are one of the millions of people who re-use user-names and passwords over multiple sites, you’d better change your login info on all accounts. This time do it properly, with a password manager. Better late than never, eh!
The Reddit system was compromised through former employee accounts which were “protected” with SMS-based two-factor authentication.
SMS-based two-factor authentication is more secure than using a password alone. But it is relatively easy to break through. For instance, an attacker can transfer a phone number by supplying an address, last 4 digits of a social security number and perhaps a credit card – exactly the type of data that is widely available on the dark web thanks to large database breaches like Equifax.

 Leave a Comment » |
Leave a Comment » |  2-factor authentication, computers, hacking, internet, OMG, phone hacking, Reddit, World Wide Web | Tagged: 2-factor authentication, computers, computing, hacking, internet, Reddit, web, World Wide Web |
2-factor authentication, computers, hacking, internet, OMG, phone hacking, Reddit, World Wide Web | Tagged: 2-factor authentication, computers, computing, hacking, internet, Reddit, web, World Wide Web |  Permalink
Permalink
 Posted by Martin X
Posted by Martin X
02/08/2018

Earlier versions of The List have been posted in other locations including Amsterdam. pic from the Guardian
An artwork featuring a list of the 34,361 refugees and migrants who have lost their lives trying to reach Europe has disappeared or been destroyed in Liverpool.
The List was created for World Refugee Day. Compiled and updated each year by United for Intercultural Action – an anti-discrimination network of more than 560 organisations across Europe – The List traces information relating to the deaths of 34,361 refugees and migrants who have lost their lives within or on the borders of Europe since 1993.
Since 2007, in collaboration with art workers and institutions, Istanbul-based artist Banu Cennetoğlu has produced up-to-date and translated versions of The List using public spaces such as billboards, transport networks and newspapers.
The List was posted on hoardings outside a building site in Liverpool’s Chinatown as part of Liverpool Biennial art festival. But now it has disappeared! On Wednesday the festival tweeted this message:
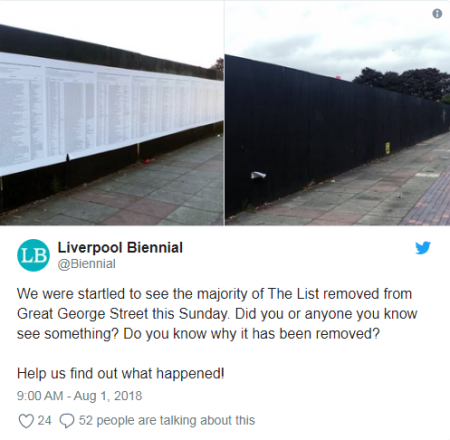
The List was posted on hoardings on Great George Street with the permission of the site owners. The city council has stated that it was not removed by its workers, whether deliberately or by accident – it had been suggested that council workers might have taken it down, misidentified as illegally fly-posted. The council and the developers who own the site have been examining CCTV for clues as to who removed it on Sunday.
What is the List?
Since 1993, activists at the network United for Intercultural Action have made a record of every reported instance in which someone has died trying to migrate into Europe. In all, 61 deaths were recorded in 1993; 3,915 were recorded in 2017.
What sources did they use?
The small team, based in the Netherlands, drew on reports in the local, national and international press, as well as NGO records. Though the vast majority of people died during en route for Europe – most of them at sea – the List also points out that hundreds died in custody, and hundreds more took their own lives. Most deaths recorded on the List are anonymous.
How many deaths have been recorded?
As of 5 May 2018, the figure stood at 34,361. But activists acknowledge that the List is neither definitive nor comprehensive. The real number is likely to be far higher, as many thousands of people will have died without trace during sea and land journeys over the years.
[from the Guardian]
United for Intercultural Action, faced with a lack of official data, gathered newspaper articles, NGO records and coastguard reports to collect details of the deaths of migrants travelling to Europe since the early 1990s. While most of the deaths happened at sea, more than 1000 happened in detention blocks, asylum units and town centres. 400 died at their own hand, over 600 violently killed by someone else. Cause of death is described quite graphically: such as “tortured by Turkish border guards near Iskenderun (TR) while trying to cross Syrian-Turkish border” and “drowned, bodies found in advanced state of decomposition 20 miles north of Zurawa LY)”.
In a statement the Liverpool Biennial said: “It is timely and important to make The List public during a global refugee crisis. We were dismayed to see it had been removed on Saturday night and would like to know why. The List has been met with critical acclaim and we are doing everything we can to reinstate it.”
To help assimilate The List across the internet, I have uploaded a pdf format copy of The list here. (The Guardian are also hosting a copy here – they’ve got a lot more available bandwidth than me, so it’d only be fair to try them first, but I’m here as a back-up if required! Happy to help!) Feel free to reproduce this link as widely as possible. Please mention ihatehate.wordpress.com and www.unitedagainstracism.org.

 Leave a Comment » |
Leave a Comment » |  asylum, Banu Cennetoğlu, Europe, immigration, Liverpool Biennial, OMG, refugees, United for Intercultural Action, World Refugee Day | Tagged: art, asylum, Banu Cennetoğlu, Europe, Liverpool, Liverpool Biennial, UK, United for Intercultural Action, World Refugee Day |
asylum, Banu Cennetoğlu, Europe, immigration, Liverpool Biennial, OMG, refugees, United for Intercultural Action, World Refugee Day | Tagged: art, asylum, Banu Cennetoğlu, Europe, Liverpool, Liverpool Biennial, UK, United for Intercultural Action, World Refugee Day |  Permalink
Permalink
 Posted by Martin X
Posted by Martin X
02/08/2018

Google has a new logo and updating its image – but under the surface it’s still that pre-2010 half-evil censor
Eight years after Google pulled out of the censored Chinese internet, they’re back. It’s been reported that the company is working on a mobile search app that would block certain search terms and allow it to reenter the Chinese market.
Google has engaged in the China-controlled internet space before: but in 2010 it pulled out, citing censorship and hacking as reasons. It didn’t pull out completely – it still offered a number of apps to Chinese users, including Google Translate and Files Go, and the company has offices in Beijing, Shenzhen and Shanghai – But the largest of its services – search, email, and the Play app store – are all unavailable in the country.
Google co-founder Sergey Brin told the Guardian in 2010 that his opposition to enabling censorship was motivated to his being born in Soviet Russia. “It touches me more than other people having been born in a country that was totalitarian and having seen that for the first few years of my life,” he said as Google exited the Chinese market after 4 years of cooperating with the authorities.
But now they’re back, working on a mobile search app that would block certain search terms and black-listed material. The app is being designed for Android devices.
According to tech-based news site The Information, Google is also working on a censored news-aggregation app too. The news app would take its lead from popular algorithmically-curated apps such as Bytedance’s Toutiao – released for the Western market as “TopBuzz” – that eschew human editors in favour of personalised, highly viral content.
Patrick Poon, China Researcher at Amnesty International, called Google’s return to censorship “a gross attack on freedom of information and internet freedom.”
In putting profits before human rights, he said, Google would be setting a chilling precedent and handing the Chinese government a victory.
This is important because many computer users will set a search site as their homepage and even find content by entering key-words into the url bar of their browser. Because of Google’s ubiquity, it is frequently set as default search engine on browsers, meaning that millions of users will find that their experience of the internet is that delivered through the lens of Google. If that lens is smudged or cracked by censorship, all these users’ internet experience is skewed. So it is essential to highlight the fact that Google is not the neutral, trustworthy agent that many users think it to be.
GreatFire, an organisation that monitors internet censorship and enables circumvention of the “Great Firewall of China”, said the move “could be the final nail in the Chinese internet freedom coffin” and that “the ensuing crackdown on freedom of speech will be felt around the globe.”

 Leave a Comment » |
Leave a Comment » |  censorship, China, computers, free, google, hacking, internet, OMG, politics, technology | Tagged: censorship, China, computers, democracy, dictatorship, dissent, dissident, free speech, freedom, google, great firewall of china, greatfire, hacking, internet, police state, search, technology, World Wide Web |
censorship, China, computers, free, google, hacking, internet, OMG, politics, technology | Tagged: censorship, China, computers, democracy, dictatorship, dissent, dissident, free speech, freedom, google, great firewall of china, greatfire, hacking, internet, police state, search, technology, World Wide Web |  Permalink
Permalink
 Posted by Martin X
Posted by Martin X
31/07/2018

Corbyn risks his party being torn apart if he can’t sort out this anti-semitism business (pic from the Independent)
What does anti-semitic mean? The top three online dictionaries (of a Google search) say:
anti-Semitism discrimination against or prejudice or hostility toward Jews (www.dictionary.com)
anti-Semitism Hostility to or prejudice against Jews (oxforddictionaries.com)
anti-Semitism the strong dislike or cruel and unfair treatment of Jewish people (dictionary.cambridge.org)
Well, that seems simple enough, right? Unfortunately, it isn’t that simple. Some people want the term antisemitic to cover a lot more than anti-Jewishism. And it’s tearing the Labour party into strips when Britain badly needs a working Opposition to the Conservative government.
So what is the problem? Some people want the Labour party to adopt an “official” international definition of anti-semitism. The definition they have chosen to push is that of the International Holocaust Remembrance Alliance (IHRA). Their definition is:
Anti-Semitism is a certain perception of Jews, which may be expressed as hatred towards Jews. Rhetorical and physical manifestations of anti-Semitism are directed towards Jewish or non-Jewish individuals and/or their property, towards Jewish community institutions and religious facilities.
Even this definition isn’t too bad. But the main problem is the examples that go with the definition. These include “Denying the Jewish people their right to self-determination, eg by claiming that the existence of a state of Israel is a racist endeavour,” and “Drawing comparisons of contemporary Israeli policy to that of the Nazis.” Basically, criticism of the state of Israel should be viewed as anti-Semitism, as should any equivalence of their racist policies and those of Nazi Germany.
Why should criticising Israel be labelled anti-Semitic? Generally it is accepted that anti-Semitism is wrong. So now criticising Israel is wrong too? That country can do no wrong? And why is it wrong to point out that Israel’s foreign and domestic policies are racist? I mean, those policies are racist, inasmuch as they are hostile to Palestinians. And how exactly does pointing out this racism deny the Jewish people their right to self-determination? Israel is denying Palestinians their right to self-determination… but to point that out is anti-Semitic? My head’s starting to hurt.
The organisation that first drafted this definition, the European Monitoring Centre on Racism and Xenophobia, recognized it was contentious – it drafted but never adopted the definition. And the UK government, which has adopted the “working definition” and the examples, was warned by the Commons home affairs select committee in October 2016 that in the interests of free speech it ought to adopt an explicit rider that it is not antisemitic to criticise the government of Israel, or to hold the Israeli government to the same standards as other liberal democracies, without additional evidence to suggest antisemitic intent (the government sadly ignored this advice).
Unfortunately for the Labour Party and its leader, some party members and supporters of the leader have come out with some awful stuff on this subject. Peter Willsman, for instance, has said some stuff that is just plain wrong and he needs to resign. But the party should not adopt the IHRA definition. And if supporters of Israel don’t like that country’s policies being criticised, maybe they should call for those policies to be changed. To be made less racist. Less likely to be compared to those of that old Nazi Adolf Hitler.

 Leave a Comment » |
Leave a Comment » |  anti-semitism, Israel, Jeremy Corbyn, Labour, nazism, OMG, politics, UK | Tagged: anti-semitism, Corbyn, Jeremy Corbyn, Labour, labour party, nazism, politics, UK |
anti-semitism, Israel, Jeremy Corbyn, Labour, nazism, OMG, politics, UK | Tagged: anti-semitism, Corbyn, Jeremy Corbyn, Labour, labour party, nazism, politics, UK |  Permalink
Permalink
 Posted by Martin X
Posted by Martin X
20/07/2018
Don’t wanna be an american idiot? Too late Donald!
Ain’t it grand, how any idiot can game Google results and show the world who really is the idiot?
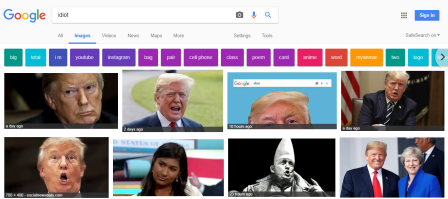
That’s what activists have been doing: do a Google image search for the word “idiot” and you get a fine selection of Donald Trump pictures!
This is how it works:
According to Inquisitr, part of the reason for this result is that several English articles published last week included the Green Day song titled “American Idiot” in the headline in relation to Donald Trump and his trip to England; (protestors were actually using the song in the protests). This meant that images were likely titled to describe the article and used the terms “American Idiot” and Donald Trump as descriptives in the image metadata as well as in the article content. As a result, Google’s algorithm has paired these terms together, and with so many people reading and sharing these articles, it has pushed its relevance to the top of the search results.
When you type the word “idiot” into Google’s image search, Trump is the first returned result. This is partly because the Green Day song American Idiot was used by protesters to soundtrack his trip to London. But since then there’s also been a concerted campaign to capitalize on that association, and manipulate Google’s algorithm, by linking the word to the picture. Mostly this involved people upvoting a post containing a photo of him and the word “idiot” on Reddit. [from theguardian.com]
This trick has been used many times before. For instance, there was a spate of hook-nosed caricatures posted with the single word “Jew”, which resulted in an Image Search for “jew” returning the hook-nosed caricature.
And it was used by Trump fans to associate the word “rapist” with pictures of Bill Clinton.
Many of these were rudimentary, almost meaningless. “RAPIST! RAPIST! RAPIST! RAPIST!” “Today this rapist turns 70. Happy Birthday, rapist.” Most originated from the notorious Reddit forum TheDonald, where fans of Trump congregated to spread his gospel of doing whatever you like, screw the consequences.
The forum moderators would pin a post to the top of the forum to encourage others to upvote it, and the swell of upvotes would push it to the front page of Reddit, which already styles itself “The front page of the Internet”, causing it to leap up to the top row of Google images.
They also did it with an image of Michelle Obama with features Paintshopped to look like an ape. And the TheDonald team did it with the CNN logo and the words “fake news”.
So it’s kind of fitting that the trick has now been turned on Trump and his idiotic fans!
So is there a moral to be learnt from this story? Of course not! The internet is utterly amoral, as are those of us who spend too much time in it. Who knows who will be belittled and demonized next? And that’s probably the best thing about it – he who demonizes today may be demonized tomorrow. The internet giveth and… well, it don’t giveth anything but it demands its pound of virtual flesh!

 Leave a Comment » |
Leave a Comment » |  An American Idiot, Donald Trump, Green Day, idiot, London, OMG, Trump, UK, US/UK, USA | Tagged: american idiot, Donald Trump, google, Green Day, idiot, internet, London, Trump, UK, USA |
An American Idiot, Donald Trump, Green Day, idiot, London, OMG, Trump, UK, US/UK, USA | Tagged: american idiot, Donald Trump, google, Green Day, idiot, internet, London, Trump, UK, USA |  Permalink
Permalink
 Posted by Martin X
Posted by Martin X
19/07/2018

Just found this download link for Julian Assange’s 2012 book Cypherpunk: Freedom and the Future of the Internet. I found it literally less than thirty minutes ago, so I’m posting it here before I’ve had a chance to read it myself. Once I have, I’ll tell you what I think of it. In the meantime, check it out for yourselves! And here is an excerpt from a review by Marienna Pope-Weidemann at http://www.counterfire.org:
A watchman’s shout in the night
Since the infamous PRISM surveillance system was exposed by the NSA analyst Edward Snowden, the existence of what the cypherpunks have long called ‘the transnational surveillance state’ is beyond doubt. Conspiracy has become reality, and paranoia has become the number-one necessity of investigative journalism.
Cypherpunks: Freedom and the Future of the Internet, published last year, describes itself as ‘a watchman’s shout in the night’. An apt description, given everything we have learned lately. What the book is trying to hammer home is the immense importance of the internet as a new political battleground: how it is structured, monitored and used has serious ramifications for political organisation, economics, education, labour, culture and just about every other area of our lives, because increasingly, their world is our world. And if knowledge is power, and it is never been as ubiquitous as it is in cyberspace, there is a great deal at stake.
Who are the cypherpunks?
Begun by a circle of Californian libertarians, the original cypherpunk mailing list was initiated in the late 1980s, as individuals and activists, as well as corporations, started making use of cryptography and, in response, state-wide bans were introduced (p.64). For the cypherpunks, the use of encryption for anonymity and secure communication was the single most important weapon for activists in the internet age.
Their rallying cry was ‘privacy for the weak, transparency for the powerful’; the dictum to which Wikileaks has dedicated itself. As discussed in the book, the subsequent evolution of the internet has taken it in the opposite direction: citizens, politically active or otherwise, law-abiding or otherwise, have lost all right to privacy, while the powerful hide increasingly behind secret laws and extrajudicial practices.
Cypherpunks is a collective contribution of four authors, three of them leading figures in the cypherpunk movement. First we have Julian Assange, who needs less and less introduction as time goes by (there are even two films now devoted to this problematic figure, the independent Australian feature, Underground, and the highly inaccurate box-office disaster We Steal Secrets). Assange has been hacking since the age of seventeen, when he founded the Australian group, the International Subversives, and wrote down the early rules of this subculture: ‘Don’t damage computer systems you break into (including crashing them); don’t change the information in those systems (except for altering logs to cover your tracks); and share information.’ Next we have German journalist Andy Müller-Maguhn of the Chaos Computer Club, co-founder of European Digital Rights and writer for Bugged Planet. Jacob Appelbaum, also a member of the Chaos Computer Club, is the developer who founded Noisebridge, an award-winning educational hackerspace in San Fransisco and international advocate for the Tor Project. Finally, we have the co-founder of the La Quadrature du Net advocacy group, Jérémie Zimmerman, a leading figure in struggles for net neutrality and against the Anti-Counterfeit and Trade Agreement (ACTA) who does not seem to be able to get on a plane without being harassed by government officials over his ties to Wikileaks.

Julian Assange, founder of Wikileaks, has been holed up in the Ecuadorian embassy in London since 2010 to avoid extradition to Sweden and USA. Pic from http://www.extremetech.com

 Leave a Comment » |
Leave a Comment » |  Andy Müller-Maguhn, assange, computers, cypherpunk, Ecuador, internet, Jacob Appelbaum, Jérémie Zimmerman, julian assange, OMG, Sweden, USA, Wikileaks | Tagged: Andy Müller-Maguhn, assange, cypherpunks, dissent, dissident, Ecuador, Jacob Appelbaum, Jérémie Zimmerman, jeremie zimmermann, julian assange, USA, whistleblowers, Wikileaks |
Andy Müller-Maguhn, assange, computers, cypherpunk, Ecuador, internet, Jacob Appelbaum, Jérémie Zimmerman, julian assange, OMG, Sweden, USA, Wikileaks | Tagged: Andy Müller-Maguhn, assange, cypherpunks, dissent, dissident, Ecuador, Jacob Appelbaum, Jérémie Zimmerman, jeremie zimmermann, julian assange, USA, whistleblowers, Wikileaks |  Permalink
Permalink
 Posted by Martin X
Posted by Martin X
19/07/2018

NATO heads of state all looking at one thing – except Trump, who has something something else in his sights. As usual, eh!
In between rounds of golf and tea with the Queen, US president Donald Trump has told the world that he considers Russia as a more valuable ally than NATO and has called into question whether the NATO mutual defense agreement still stands.
Trump launched his assault on his NATO “partners” immediately, criticising Germany’s reliance on Russian natural gas, and other members’ failure to commit adequate funding for their membership. He made it clear that he prefers Putin and Russia over some of his “allies”, and even called into question the doctrine of mutual defense. In a Fox News interview, newsman Tucker Carlson asked the Prez why the U.S. should protect a country like Montenegro, which joined NATO last year; and Trump replied that he has asked himself the same question.
“Montenegro is a tiny country with very strong people,” Trump said. “They’re very aggressive people, and they may get aggressive, and congratulations, you’re in World War III. But that’s the way it was set up.”

Trump shoves Montenegro Prime Minister Dusko Markovic out of his way at NATO summit
When Montenegro joined NATO, Russian president Putin didn’t like it at all. So really it shouldn’t be too much of a surprise that Trump doesn’t like it either. He declared that Russia did not pose any kind of danger to the US, contradicting everything he has been told by his military advisors. The White House tried to put a different spin on it, but the facts are clear: Trump has got a very “special” relationship with Putin – more “special” than the “special relationship” US and UK leaders are supposed to have enjoyed at least as far back as Ronald Reagan and Margaret Thatcher back in the 1980s.
This also shouldn’t really be a surprise: in London Trump made it clear that his favourite thing in the British government was Boris Johnson, former Foreign Secretary who has quit his job over Brexit. Trump said that prime minister Theresa May’s Brexit plans have scuppered any chance of a post-Brexit trade deal between the US and UK. So Trump clearly wants May out of office and Johnson in. Then the special relationship can be resurrected.
So, what did Trump achieve on this trip to Europe? He offered the hand of friendship to Vladimir bloody Putin and Boris bloody Johnson. He belittled or ignored his allies in NATO. He undermined the British prime minister. He called into question the principles on which NATO was founded. And he had tea with the Queen.
All in all, a profitable few days. Thanks Mr Trump! Come back soon!

 Leave a Comment » |
Leave a Comment » |  Angela Merkel, Donald Trump, Dusko Markovic, Germany, May, Montenegro, NATO, OMG, Putin, Russia, Russian Federation, Theresa May, Trump, UK, US/UK, USA, Vladimir Putin | Tagged: Germany, markovic, May, merkel, Montenegro, NATO, Putin, Russia, Russian Federation, Trump, UK, united kingdom, USA |
Angela Merkel, Donald Trump, Dusko Markovic, Germany, May, Montenegro, NATO, OMG, Putin, Russia, Russian Federation, Theresa May, Trump, UK, US/UK, USA, Vladimir Putin | Tagged: Germany, markovic, May, merkel, Montenegro, NATO, Putin, Russia, Russian Federation, Trump, UK, united kingdom, USA |  Permalink
Permalink
 Posted by Martin X
Posted by Martin X
18/07/2018

Work and Pensions Secretary Esther McVey said that the poor could eat cake. The last woman in a position of authority to make a comment like that got her head chopped off. An act that I in no way endorse!
The British Department of Work and Pensions has given in to pressure from anti-poverty charities and will pay arrears owed to sick and disabled benefit claimants who were cheated out of thousands of pounds after what is described as “a series of bureaucratic errors.”
The under-payments, some of which date back to 2011, happened when claimants of contribution-based Employment and Support Allowance were not told they would be better off if they claimed income-based ESA. This “mistake” resulted in at least 70,000 claimants missing out on up to £20,000 each.
Child Poverty Action Group challenged the under-payments in a judicial review, but the DWP has accepted that it was in the wrong and will not contest the review. A CPAG lawyer welcomed the DWP’s change of heart but added it “shouldn’t be necessary to take a government department to court to achieve justice for people who have been failed by officials making errors.”
The decision quickly followed the publication of a report by cross-bench public accounts committee. The report said there was a “culture of indifference” at the DWP, and criticised its failure to obtain legal advice when transferring claimants to ESA, failed to make basic checks and ignored evidence and complaints that the process was flawed.
Committee chair, Meg Hillier MP, welcomed the U-turn, saying she had been appalled by the DWP’s failure to correct its errors.
But the DWP still refuses to pay compensation to claimants who were wrongly denied related benefits such free prescriptions as a result of the “error”. Big surprise!

 Leave a Comment » |
Leave a Comment » |  Department of Work and Pensions, dwp, esther mcvey, government, OMG | Tagged: Department of Work and Pensions, dwp, esa, esther mcvey |
Department of Work and Pensions, dwp, esther mcvey, government, OMG | Tagged: Department of Work and Pensions, dwp, esa, esther mcvey |  Permalink
Permalink
 Posted by Martin X
Posted by Martin X




 Posted by Martin X
Posted by Martin X 














