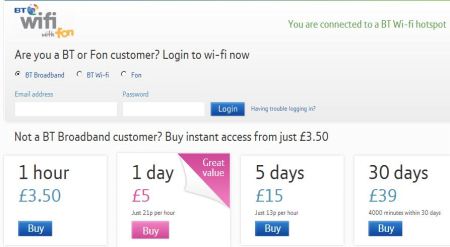
I’ve been using a BTWifi-with-FON hot spot for internet access. The way it works is: user clicks on connect in wifi manager, then browses to https://www.btopenzone.com:8443/home, fills in the form with User email address and Password. This lets the user access the internet for anything between 1 and 3 hours, depending on time of day and day of week. Then access runs out and the user must sign in again.
If you’re using the hotspot for an extended period of time, having to go through this palaver can be pretty irritating. Luckily I’ve started learning python, which is an excellent language for automating this kind of procedure. So this is the script I have written to make my use of the hot spot a little less stressful:
import pymsgbox
import requests
import time
import sys
def log_in():
url = “https://www.btopenzone.com:8443/tbbLogon”
values = {“username”: “foo@bar.com”,
“password”: “foobar”}
requests.post(url, data=values)
def vpn_check():
p = requests.get(“http://www.icanhazip.com/”)
ip = p.text.rstrip()
if ip == “!!!.!!!.!!!.!!!”:
# uncomment line below for vpn connection confirmation
#pymsgbox.native.alert(“Logged into VPN”, t)
sys.exit(0)
test_url = ‘https://www.btopenzone.com:8443/home’
response = requests.get(test_url)
html = response.content
page_start = str(html[0:1000])
t = time.strftime(“%X”)
if “DANTE” not in page_start:
vpn_check()
pymsgbox.native.alert(“Signed OUT, click me to sort it”, t)
log_in()
#uncomment following lines for signed-in confirmation
#else:
#pymsgbox.native.alert(“Signed in”, t)
At the top of the script I import the modules I need. Pymsgbox provides pop-up message functionality. Requests handles the webpage parsing and filling in the online form. Time enables the script to display the time in the pop-up boxes. And it uses sys so it can drop out of the vpn_check() function.
Next up, it defines the log_in() function. Although the user navigates to https://www.btopenzone.com:8443/home to sign in, the form url is http://www.btopenzone.com:8443/tbbLogon. The values to be provided are username (the user’s email address) and password (a password). According to the ancient custom, here I have used foo@bar.com as user’s email address, and the password is foobar. Requests delivers these values to the form url.
The script goes on to define the vpn_check() function. As this is a public wifi hotspot I use a vpn service, Invisible Browsing VPN aka ibVPN. The vpn_check() function checks whether the computer is using a vpn by comparing the public ip address to that used by the vpn service. Here the vpn ip address is represented by X.X.X.X. If the ip address is the same as the vpn’s address, the script terminates.
Now the script proper starts. It checks whether we are already signed in to the BTWifi service. This is performed by going to a particular url – https://www.btopenzone.com:8443/home and examining the html source code. If the computer is already signed in, that webpage will redirecte us to http://home.bt.com/bt-wifi-01364197228851. The first thousand characters of that page’s html source code contains the string “DANTE”. If the string is present, we know we are signed in and the script terminates. If the string is not present, the computer is either using a vpn or is not signed in to BTWifi.
So the script performs the vpn_check(), using the online service at http://www.icanhazip.com to check the computer’s public ip address. If this matches the vpn ip address, X.X.X.X we know the computer is signed into BTWifi and using the vpn. If the public ip address does not match the vpn ip address, we deduce that we are not using the vpn and therefore we are not signed in. So a pop-up message tells the user that we are not signed in, and if the user wants to sign in he should click the OK button. If he clicks the button, the script goes on to the log_in() function, to sign in to BTWifi.
With log_in() the script navigates to the sign-in form at https://www.btopenzone.com:8443/TBBLogon, and fills in the form fields with the values. We are signed in, and the script terminates.
On my computers, which use either Windows 7 or Windows 8.1 operating systems, I have scheduled this script to run every 5 minutes. It regularly checks the computer’s signed-in status, putting up a message if the computer is no longer signed in. The message box says : “Signed OUT, click me to sort it.” Click the button and the script signs into the wifi. This is much less stressful than having the palaver of going to the wifi sign-in page and dealing with the form.
This script is very much a work in progress. Look at the code and you will see a number of lines commented out. Uncommented, these lines of code provide confirmation when the script finds out it is signed into the wifi or using the vpn. These were used for testing. I intend to comment out the message that we are not signed in, and have the script deal with it in the background. This will allow me to work online or watch a streaming video without interruption – unless a connection problem arises!
I have found that sometimes there is a connection error, python raises an exception and program exception is interrupted. If I’m running the script in IDLE the exception output is printed in the interactive shell, but if it is working in the background, scheduled to run every 5 minutes I won’t get any error info. I am going to see if a try/except block will deal with it. I plan to have basic error info printed in a pymsgbox pop-up. I can then investigate what’s up with the connection, whether the problem is with the hot-spot or my own hardware. Sometimes when I’m experiencing connection problems, I run diagnostics on network connection and Windows resets my network adapter and that fixes the problem!
If anyone has any suggestions about this script please let us know in Comments. Constructive criticism is welcome. If anyone else finds this helpful (perhaps you also use a BTWifi-with-FON hot spot?), let us know! And maybe buy me a coffee…? 🙂





 Posted by Martin X
Posted by Martin X